This website uses cookies. By continuing to browse the site, you are agreeing to our use of cookies
What is Cloud Security? How to Secure your Cloud?
Digital IT Operations
October 26, 2022
Cloud security refers to the protection extended to all cloud-based data, applications, and infrastructure from cyber threats and attacks.
With more devices, services, and data using the Cloud continually, security should take enter stage, and rightly so. As the trend accelerates further with the growing deployment of Industry 4.0, IoT, etc., fuelled by 5G, no business can operate without an adequate security overwatch, irrespective of the nature of the Cloud used. And our ever-growing reliance on the Cloud for the modern world to operate needs the highest levels of protection.
Add to those certain myths that many enterprises surprisingly believe in – the Cloud is a data center in the sky, the onus is on the security team to fix all problems, and Cloud security needs human intervention. Once these myths get debunked in the boardroom, Cloud security can be addressed in the manner that it should: seriously and pragmatically, and by encompassing a wide suite of technologies, policies, controls, and services. Essentially, this entails staying vigilant and impenetrable against both internal and external cybersecurity threats and attacks on a 24/7/365 basis.
The Importance of Cloud Security
In a nutshell, Cloud security, also referred to as cybersecurity, encompasses a wide variety of suite of technologies, policies, controls, and services that protect everything prevalent on the Cloud – data, applications, and infrastructure.
Further, in the interest of enterprises and their customers, governments worldwide are also taking a hard look at various aspects of Cloud security and laying down stricter protocols to govern and thwart attacks of today and tomorrow while ensuring Business Continuity (BC).
Typical Cloud infrastructure can consist of – physical networks, data storage and servers, virtualization frameworks, Operating Systems (OS), Middleware, Runtime environments, applications, and end-user hardware. With such a complex ecosystem to consider, a loophole can be an easy invitation for any number of ways an attacker can exploit the Cloud. Consider the following statistics that show cloud security’s importance in stark numbers.
- Every 39 seconds, there is a new web-based attack across the world
- Globally, 30,000+ websites are hacked daily
- 64% of companies worldwide have experienced at least one form of a cyber attack
- In 2021, 22+ billion records were breached
- In 2021, ransomware cases grew by 92.7%
- 94% of all malware circulates via email
- 24,000+ malicious mobile apps are blocked daily
(Source: Techjury)
The Challenges around Cloud Security
Going forward, the numbers will only grow exponentially because, in this deadly game of cat and mouse, security technologies and protocols try to stay a step ahead of the attackers and vice-versa. Moreover, not all enterprises approach Cloud security in a holistic sense. Others lack the technical expertise or need adequate funds to ensure a fool-proof solution. Whatever the reason, even the minutest hole in Cloud security can render the entire Cloud porous to attacks of all sizes and complexity. The fallout could be anyone’s guess.
The risks and challenges to be addressed while considering Cloud security and the overall Cloud infrastructure security include data breaches, visibility, dynamic workloads, multi-tenancy, abusive use, hijacking, misconfigurations, unsecured APIs, access control – especially in the current era of remote working and WFH, control pane security and compliance and auditing. Almost every day in the news, we hear businesses and individuals across the world compromised by malicious states and hackers with various modus operandi – and it is the Cloud that is the medium in which all the action happens. Little wonder, it is no rocket science that today, every CIO’s focus is to secure the Cloud to the max!
5 Tips for Securing your Cloud Ecosystem
When it comes to securing your Cloud ecosystem in the best possible manner, it pays to get the best approach, expertise, and technology deployed. However, that is an ideal scenario. A broader guide that should be followed for Cloud security includes a 5-pointer program.
- Cloud workload protection: Cloud workloads increase the attack surface exponentially. Protecting workloads requires visibility and discovery of each workload and container events while securing the entire cloud-native stack, on any cloud, across all workloads, containers, Kubernetes, and serverless applications that enable enterprises to build, run, and secure cloud applications from production to deployment.
- Data encryption: One of the most effective ways to protect data is to encrypt it end-to-end. Depending on unique business requirements, it is prudent to have additional levels of protection in the form of multi-factor authentication (MFA), continual monitoring and vulnerability assessment, micro-segmentation, and detection and response capabilities.
- Security posture/governance: It is critical to determine your Cloud infrastructure’s security posture with a strict policy-adhered and rule-based governance that works with all the stakeholders. Such a posture can help identify and prevent misconfigurations and control plane threats and eliminate blind spots while ensuring compliance across every piece of infrastructure – the data that flows through it, the devices that access it, and the apps that process it.
- Unified Visibility: It is another way to detect misconfigurations, vulnerabilities, and various security threats across multi-cloud environments. This, when implemented along with continuous intelligent monitoring of all cloud resources, provide invaluable actionable insights and steps for rectification.
- Threat Intelligence with real-time threat detection: As stated earlier, threats are constantly evolving, and thereby, the onus is on enterprises to stay protected as they continually shape-shift. Threat intelligence helps anticipate upcoming threats and prioritize them effectively towards pre-emptive actions. With automation and AI, threat intelligence can be significantly augmented and offer a better shield with enhanced contextualizing, quarantining, and investigating, even as it helps build a knowledge repository that gets constantly updated.
What is the Future of Cloud Security?
Keeping in mind the persistently evolving and growing nature of threats, it’s a race against time for enterprises. For something as omnipresent as the Cloud, Cloud security solutions become both the arrowhead and the hammer in this constant battle. This is why, at Hexaware, our approach to Cloud security and its future is as comprehensive as possible.
Our Cyber Security and Resilience Services (CSRS) come with a wide range of integrated security solutions in various layers of consulting, engineering, and operations focused on cognitive intelligence, automation, and response, giving you a complete view of their security front 24/7. With CSRS, you can now adopt and transform security in various data lifecycle stages with near real-time visibility, high-powered analytics, and intelligence against the most sophisticated threat vectors. Aided by a tailored assurance framework, you can put a hard light on your current security posture and devise a way forward with a unified framework solution (combined control matrix covering NIST, ISO 27k, PCI DSS, Cloud CSA, etc.) to address any GRC requirements.
Consulting: Hexaware Cyber Security expert team developed the GRC control Matrix having six stages covering multiple Security frameworks and standards (NIST, ISO 27000, PCI-DSS, CSA). Our framework focuses on fundamental security components’ People, Processes & Technology to significantly focus on the security triad of Confidentiality, Integrity, and Availability. To realize these, the solution offers:
- Current state assessment, audit, and performance evaluation service
- Design, implement and automate risk management
- Understand, design, customize, and rationalize frameworks to achieve a balance between conformance and performance aligning with accomplished frameworks and specific regulations such as NIST, COBIT, COSO, ISO, PCI, CSA or HIPPA, SOX, GDPR, SABSA, Kill Chain, MITRE ATT&CK
- Building resilience through business continuity, analyzing and implementing GRC automation
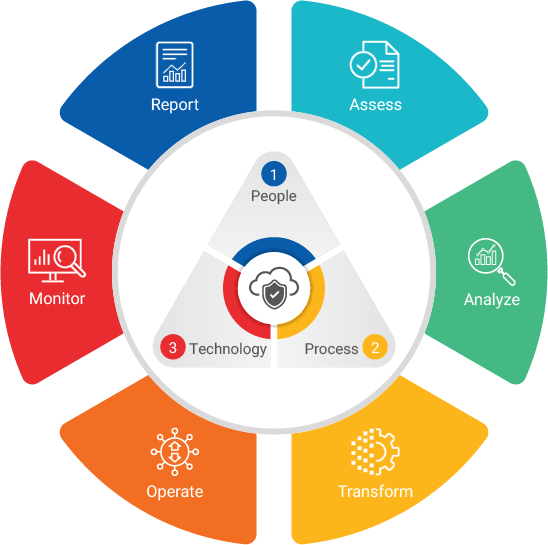
Engineering: From an engineering perspective, Hexaware’s GRC solution aims to reduce complexity and prioritize investment to minimize costs. Designed based on four blocks of Business Aligned Strategy, Cognitive Approach, Benefits Realization, and Risk Compliance, GRC is your one-stop shop for all things Cloud security.
Operations: Using Service Now, Hexaware’s GRC platform gives you a centralized process for creating and managing policies, standards, and internal control procedures – each cross-mapped to external regulations for centralized management for every detail across the entire Cloud infrastructure, thanks to in-built next-gen tools and applications for identification, assessment and continuous monitoring within and beyond.
- Establish controls and controls for owners
- Define control tests and expected results
- Establish test and control frequencies
- Identify risks: Impact and likelihood
- Prepare attestations
- Map authoritative sources to policies, procedures, controls, and risks
The fight goes on
And so does our arsenal to combat newer threat vectors. All kinds of vulnerabilities mentioned above are preventable with an effective defense strategy and a security toolkit that goes beyond methodologies. But do keep in mind we are the weakest links between the success of a Cloud strategy and the intentions of an evil mind who will use any/all means to distract, disturb and disrupt daily operations and long-term prospects. Sometimes, it all boils down to just the smallest act of negligence.
About the Author

Hemant Vijh
Hemant Vijh is EVP and Global Practice Head– Digital ITO services at Hexaware. Hemant is responsible for managing and growing Hexaware’s ITO business with a focus on product management across Digital Workplace, Hybrid Cloud, DevOps, Ops Automation, App Ops, and Cyber Security Resiliency Services. Hemant has over 25 years of industry experience and has spent a large part of his career, 15 years, at HCL, where he was involved in incubating the Remote Infrastructure Management business. He has held leadership positions in technology excellence, practice P&L management, product management, and service delivery. Before joining Hexaware, he led the global product management function for infrastructure services at HCL. Hemant holds a Post Graduate Diploma in Business Management. Along with his passion for distance running, Hemant enjoys spending time with his family and writing poetry.
Read more
Related Blogs

Digital Workplace Transformation: Strategies for the Modern Workplace
- Digital IT Operations

Ensuring Digital Workplace Security: Addressing Challenges with Best Practices
- Digital IT Operations

Software Asset Management Alongside Virtualization Technologies Can Maximize Sustainability
- Digital IT Operations

The Efficiency Engine: How Software Asset Management (SAM) Best Practices Fuel Business Growth
- Digital IT Operations

Sustainable Cost Reductions in IT: Navigating the Green IT Landscape with Hexaware
- Digital IT Operations

ISG Cost Optimization Survey Gives Deep Insights into Savings Opportunities
- Digital IT Operations
Unpacking Agility with tensai®
- Digital IT Operations

Elevating Customer Experience: Unveiling ServiceNow’s Benefits and Best Practices
- Digital IT Operations

Gen AI: Leveraging Generative AI for Augmented Test Management
- Generative AI
- Digital IT Operations

Achieving Cyber Resilience: Successful Strategies, Significance, and Benefits
- Professional Services
- Digital IT Operations

Ready to Pursue Opportunity?
Every outcome starts with a conversation







