This website uses cookies. By continuing to browse the site, you are agreeing to our use of cookies
Why Cloud-native Application Security Needs a Mindset Change?
Cloud
April 26, 2019
Application Security had generally been an afterthought and applied as an add-on feature to enterprise applications in the traditional world of monolithic architectural styles. Today, more and more organizations are embracing a cloud-native approach where software is developed and composed from containerized microservices.
According to recent research conducted by PureSec Ltd., serverless architectures have skyrocketed in the last couple of years with an annual growth rate of over 700%. With this growth, new challenges are introduced in monitoring end-to-end visibility and detection of security incidents. So, this trend has necessitated organizations to make fundamental changes in their security infrastructure and architecture.
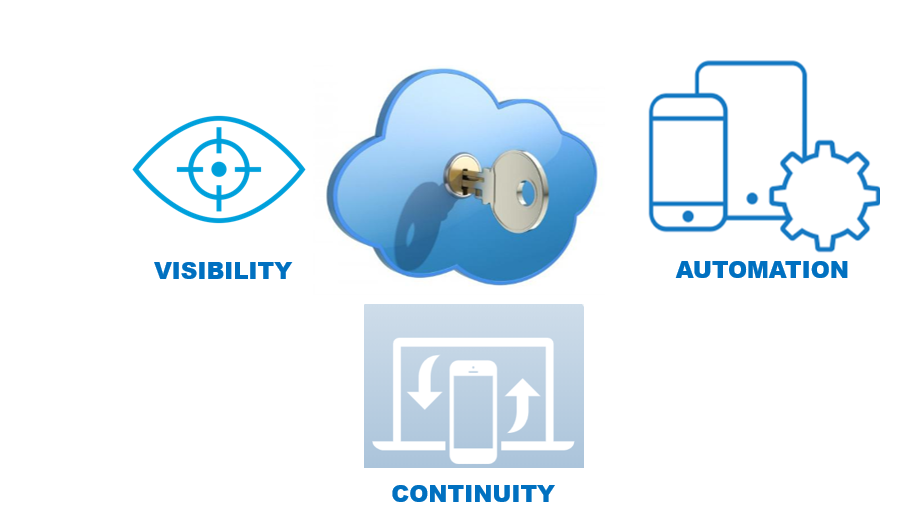
Cloud-native Application Security needs three essential elements:
let us look at some key application security challenges and feasible solutions while designing them in the cloud native context
- Lack of network security tools to monitor activity at the container levelMost traditional network monitoring tools such as Nagios, PRTG, etc. are suitable only for monitoring activity at the OS (operating system) level. In cloud-native architectures, multiple containers may potentially run services on the same OS and may start and stop these services independently. If there is no proper mechanism in place to track container activities, the administrators would lack visibility on container events.
With support available from containers such as Docker, organizations can institute internal agents that run inside each monitored container. In cases where this is not feasible, shared agents running on host systems can monitor events by invoking container APIs.
- Dynamic and elastic nature of application boundaries Cloud-native applications are highly distributed, auto scalable, and changes much faster than monolithic applications. They are also characterized by on-demand provisioning of resources.
Along with on-demand provisioning, as the cloud environment scales, enterprises must install automated threat detection components that start and stop based on container events.
- High data traffic between a large number of microservices increases application vulnerabilityApplications built on the cloud are composed of light-weight, fine-grained containers and microservices. Multiple channels consume these via higher level software abstractions. As a result, a large volume of data gets exchanged across the distributed environment. Increased data-flows expose data to attackers at multiple touchpoints. Conventional detection techniques fail to integrate seamlessly in such environments.
The risks associated with this challenge can be mitigated by the following approaches:
- Since each microservice performs specific functions, each of them should be designed to have anomaly detection mechanisms based on machine learning algorithms and trained on normal and abnormal data-flow inside and outside the services.
- Orchestration platforms such as Docker and Kubernetes have integrated secret management techniques. It must be ensured that secrets are distributed only to the containers that use them when they need them.
- Unauthorized commands (such as create, launch, kill, etc.) issued to container instances should be blocked by intercepting them.
- Frequent updates to numerous microservices enhances the risk of introducing new security holes Truly cloud-native applications are built by composing data from services offered by a diverse set of teams. Since these services are independent in principle, more frequent updates are expected to occur than a traditional architecture. Hence, there is an inherent lack of steady state system to test and certify at any point in time. Monolithic architectures view security as restricting access to application features. Whereas in the cloud, application architects must ensure that ‘each service’ is consumed via API Gateway services provided by the cloud platforms. These API Gateways provide mechanisms to integrate with identity and access management solutions to restrict access only to authorized users. Audit, monitoring, governance and incident reporting must be made at the service level.
- Lack of control over physical and network infrastructure exposes organizations to data loss and breach As more and more organizations move their applications to the cloud, administrators have lesser control on the physical and network infrastructure where their business-critical data is stored and used by the applications. According to a report submitted by Cloud Security Alliance (CSA), there is a 29 percent increase in data breaches in 2017 compared to 2016. Multiple reasons are attributed to this – inadequate access management, lack of proper backup mechanisms and denial of service attacks.
Organizations choosing to move their enterprise applications portfolio to the cloud should follow the below precautionary measures to reduce this risk –
- To prevent DDoS, make an arrangement with cloud vendors to provide geographic redundancy and data backup within the cloud
- Ensure automatic rotation of cryptographic keys, passwords and certificates
- Enhance encryption standards (in rest and transit) of business-critical data
While cloud-native software has made a paradigm shift in the way enterprise applications are architected and designed, it has brought in its own unique set of security concerns. The concerned decision makers and technology professionals need to change their traditional approach to protect their software from attack. Else, organizations will be forced to resort to reactive methods of fixing them. This can be surely avoided by taking a far-sighted view and implementing the solution approaches we discussed.
About the Author:
Devaraj Muthuvelmanickam works as a Sr.Technical Architect at Hexaware Technologies Ltd. He has more than 17 years of Software Development experience, Designing and building enterprise applications for large customers . He has worked in multiple domains including, Govt. Commerce,Finance, Telecom, Travel and Manufacturing.
About the Author

Devaraj Muthuvel Manickam
Read more
Related Blogs

Understanding Snowflake Cortex for Gen AI Applications with Sensitive Data
- Generative AI
- Cloud
- Data & Analytics

Ready to Pursue Opportunity?
Every outcome starts with a conversation