The whole IT industry is on a cloud spree in some manner or the other manner with containerization leading the way. As more and more organizations are now considering containers for application cloud replatforming to reduce TCO and get cloudified rapidly, ensuring the security of these containers has become highly critical. In this context, let us discuss a few IT industry concerns as mentioned below:
- Why are containers becoming significant while moving to the cloud?
- When should I go for containerization?
- Is a container secure?
- Which security restrictions are valid for containers?
- How to secure an application container while implementing cloud replatforming?
As the demand for containerized and cloud-native applications increases, organizations gradually realize that security is of the utmost importance when adopting to the cloud. In today’s scenario, security is the biggest concern of every other organization. People are struggling to figure out a structured way of leveraging new-edge technologies in a secure manner. Securing an application across containerization at each development stage during application replatforming is challenging. Organizations must understand this while developing their first containerized application
Nowadays, containers have become the de-facto implementation standard in the cloud journey, mainly due to their plethora of benefits (major ones can be seen in Figure 1 below). The blooming open-source community, combined with the maturity of commercial offerings has lent confidence to enterprise customers to transfer to the cloud with containers.
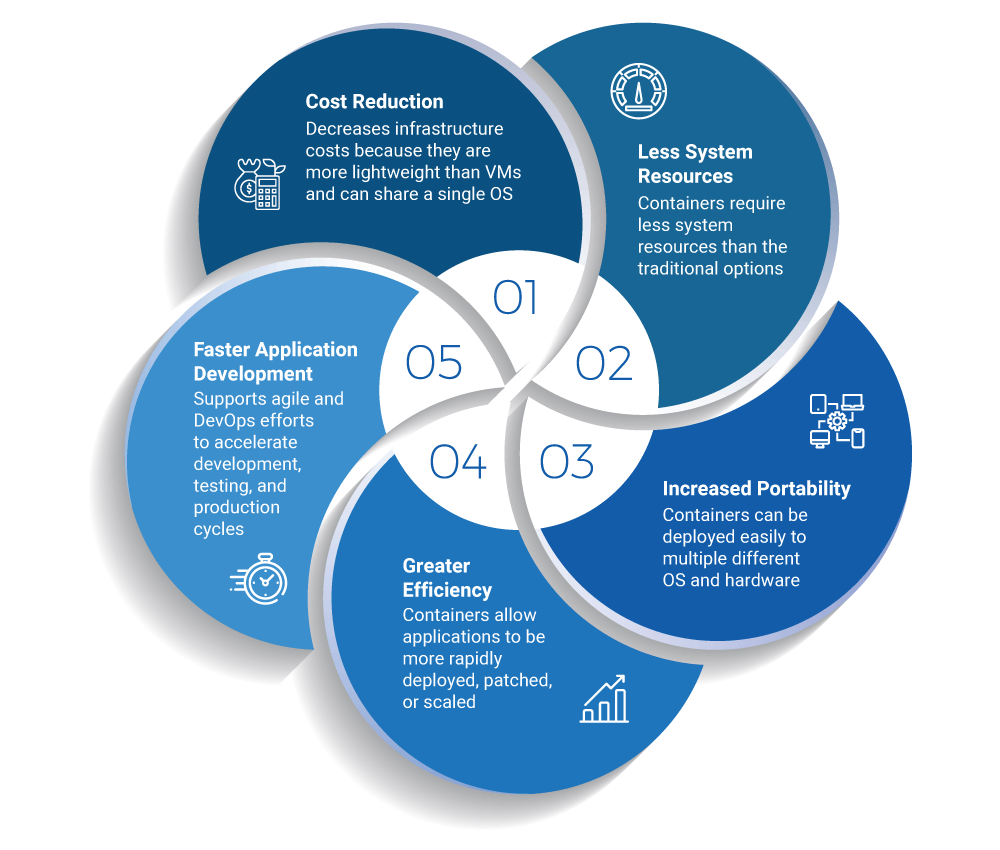 Figure 1: Pack, Ship, and Run applications as a lightweight, portable, and self-sufficient tool
Figure 1: Pack, Ship, and Run applications as a lightweight, portable, and self-sufficient tool
Though all types of applications can be containerized, it is best suited for managing web applications, especially in the Linux environment. It is most useful for front-end and middleware development and has less to offer for back-end technologies. The foremost reason behind this is that databases are optimized to interact directly on the hardware and containerization would therefore bring no gain in performance.
While there is no doubt that containerization is the most efficient and quickest way of application replatforming for the cloud, it can bring a whole lot of challenges when it comes to deploying and securing them. By breaking down your monoliths into microservices architecture with each microservice running in a separate container, the chances of having the whole app compromised due to a security vulnerability in one microservice is lesser as compared to the impact such vulnerability could cause to its monolithic version running on a virtual machine.
On the other hand, Docker (the open-sourced software platform for building applications) does not provide the strict isolation between applications that you get from a virtual machine.
The chart in Figure 2 displayed below shows the five most common container security risks you must be aware of along with the tools and best practices to help improve your security posture.
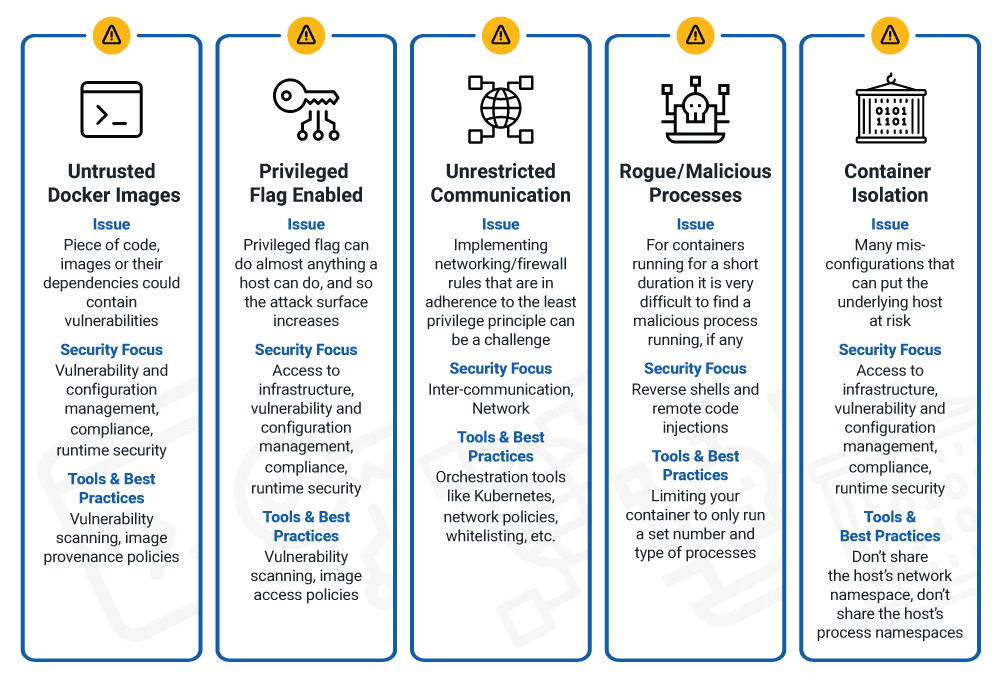 Figure 2
Figure 2
Migrating to containers is a very advantageous initiative, but it will give rewarding benefits only if you ensure the absolute security of your applications before deploying them in containers. Security before containerization is recommended rather than security measures post containerization. The benefit derived through securing before containerization is that not only does it give you a competitive edge when it comes to cloud security but also ensures seamless performance of your applications.
Hexaware’s unique product amaze® for Application achieves cloud replatforming with container security best practices applied in the recommended way – it not only helps you replatform your monolith application to the container, it also takes all measures listed above to ensure that its deployment to the cloud environment is structured and seamless. To know more about the benefits, please visit amaze® for applications.
References
- Forbes blog: 5 Modern Infrastructure Trends To Watch Out for in 2019
- Gartner
- ITOpsTimes Article: Enterprise container strategy: It’s time to jump on board
- StackRox Article: 6 Container Adoption Trends of 2020
- Tripwire Article: 60% of Organizations Suffered a Container Security Incident in 2018, Finds Study