The era of cloud is here and the market is dynamic as ever. To stay relevant in this competitive landscape, enterprises are explicitly expressing their interest in cloud adoption. What is driving this shift?
As market forces influence organizations across sectors and domains to create greater efficiencies and an enabling environment to foster innovation, they are realizing the criticality of embracing cloud-native approaches to design and host enterprise applications. This essentially means that the traditional ways of looking at business functions as separate departments driven by siloed applications hosted on on-premises infrastructure (hardware and software) is fast fading. Moreover, the conventional set up is being replaced by collaborative enterprises where business-critical data is consumed via independently deployable microservices. These services are then reused across business functions to automate manual tasks, improve efficiencies, and make inroads into new models and markets
As this transformation happens at a rapid pace, certain challenges are also introduced along the way. Monitoring, end-to-end visibility of processes, detection of security incidents, and data protection are some of those. It has necessitated organizations to make fundamental changes in their security infrastructures and architectures.
How securing cloud-native applications is different from an on-premises app
Cloud native context poses many new challenges while designing the applications for security. Some of them are listed below:
Challenges due to outdated mindset regarding monitoring tools
Traditional network monitoring tools lack the capability to track metrics and events at the container level. Cloud-native architectures, that are fundamentally based on containers and serverless infra come with the challenge of monitoring them closely based on their start and stop events. Without proper mechanisms in place to track container activities, the administrators lack visibility on container events.
Need for shared responsibility to secure applications running on public cloud
In traditional architectures, organizations completely own the hardware and software infrastructure required to host their enterprise apps. Since this changes in cloud-native apps(where infra and platform services – via IaaS and PaaS), organizations must change their processes to enable a shared responsibility model for security – part of it owned by the cloud service provider (usually at the infra level) and the rest owned by application owners from the enterprise.
In the case of applications hosted on public cloud, organization level IT administrators have lesser control over the physical and network infrastructures on which their business-critical data is stored and used by applications. This can potentially lead to inadequate access management, lack of proper backup mechanisms and Distributed Denial of Service (DDoS) attacks.
Dynamic and elastic nature of application boundaries necessitates intelligent mechanisms to detect anomalies
Cloud-native applications are known to be highly distributed, have enormous auto scalability, and are capable of faster change than monolithic applications. On-demand provisioning of resources is also one of their prominent feature. Hence, such an infrastructure may require a totally different security mechanism such as one that is equipped with automatic threat detection components (based on anomalies) and that starts and stops based on container events. In the absence of these mechanisms, requests may be routed to malicious code.
High level of interactions between microservices exposes apps to new vulnerabilities
Applications built on cloud are composed of lightweight, fine-grained services with diverse channels accessing them via front-end abstractions. Large volumes of data get exchanged across network boundaries and regions. As a result, attackers can potentially use multiple touchpoints to hack. Conventional detection techniques may be insufficient to deliver results in such scenarios.
Adoption of DevOps leading to increased frequency of production deployments exposes cloud apps to new security holes
With movement to cloud-native, the development and operations model tends to be more agile than on-premises apps. This is primarily due to on-demand availability of virtual infrastructures. While this adds significant value to the business, the ability of the steady state system to test and validate decreases substantially.
Cloud security – how to minimize risks
The diagram below shows a Gartner report on various approaches through which organizations are attempting to tackle the challenges described.
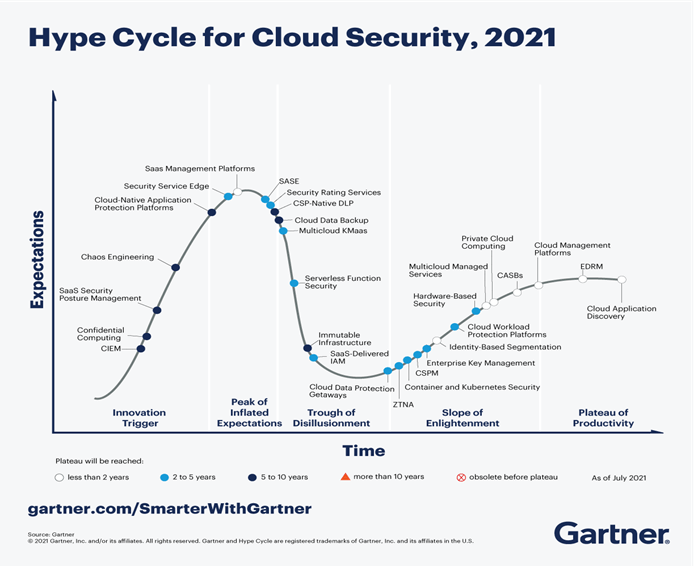
Let us understand a few of these strategies in detail below:
I. Enable Container and Kubernetes Security
With adequate container support available, organizations can establish internal agents to run inside each monitored container. In varying cases, , invoking APIs through shared agents on host systems can be useful.
To match the scaling cloud environment, it is essential for enterprises to install automated threat detection mechanisms that start and stop based on container events.
II. Use Cloud Native Application Protection Platforms (CNAPP), cloud-native off-the-shelf PaaS for secure access
CNAPPs are an integrated set of cloud-native application security tools such as tools for container scanning, infrastructure as code scanning, entitlements management and runtime cloud workload protection tools. CNAPPs enable organizations to use integrated offerings to protect the entire lifecycle of a cloud-native application
Cloud-native services facilitate easy integration with identity and access management solutions to limit access to authorized users only. Provisions for audit, monitoring, governance, and incident reporting must be made at the service level.
In addition, to reduce the risk of network attacks such as DDoS, organizations choosing to move their enterprise application portfolio to cloud, should also follow specific precautionary measures – like planning for geographic redundancy and data backups within the cloud, enable automatic rotation of passwords, and strengthen encryption standards of business-critical data
III. Develop intelligent mechanisms to handle increased complexity on cloud
Cloud-native apps are typically built following a microservices architectural approach. In such cases, each service should be designed to have anomaly detection mechanisms based on machine learning algorithms and trained on normal and abnormal dataflows inside and outside the services. Orchestration platforms such as Docker and Kubernetes have integrated secret management techniques. It must be ensured that secrets are distributed only to the containers that use them when they need them. Unauthorized commands (such as create, launch, kill, etc.) issued to container instances should be blocked by intercepting them.
Moreover, the application deployment pipelines via continuous integration/deployment mechanisms must have security scanning and automation testing included in the cycle. Implementing these through DevSecOps tools can mitigate risks.
Can cloud be as secure as on-premises?
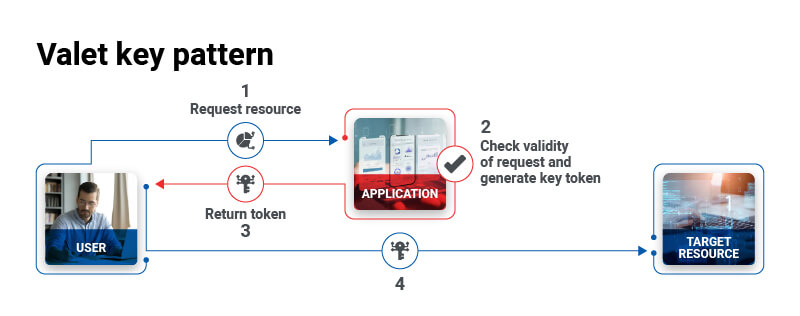
As established, in the initial stages of transitioning to cloud (from on-premises), it does appear that cloud poses new risks and vulnerabilities not applicable to on-premises applications. However, with appropriate methods and techniques, it is possible to make them as secure as applications running on on-premises infrastructures. In other words, cloud applications adhering to “secure” principles can be architected and designed to prevent malicious activity, guard against accidental events, and restrict access to authenticated users. Some of the typical techniques used are encryption, Valet Key Pattern, Gatekeeper, Throttling, etc. One of the patterns is depicted below:
Conclusion
While cloud-native software has become a differentiator in augmenting the application design and performance of enterprises, it does come with a unique set of security challenges. The concerned decision-makers and technology professionals need to change their traditional approach to protect their software from attacks and avoid a reactive approach to security threats. This can be achieved by maintaining a far-sighted view and implementing the solution approaches discussed above.
Some of the cloud native security solutions provided by Hexaware are mentioned below:
Hexaware’s Cloud-native Security Platform
It provides the controls to protect the workloads running on cloud-native platform. The features of Cloud-native Security Platform are:
-
Image Verification
Used to verify that all the images running on the platform are approved or certified and do not possess any vulnerabilities and are not susceptible to attacks
-
Immutability of Containers
Enforce the policy that containers are immutable once created and would not be alterable in case of changes.
-
Continuous Monitoring
Machine Learning-based continuous monitoring to track the new deployment of containers and any unusual traffic to the container.
Integrated Cloud Sec Ops Platform
Hexaware’s Integrated Cloud SecOps platform is a centralized platform to provide complete visibility of cloud environments. It can be used to enhance cloud security operation practices like provisioning the infrastructure, deployment, management of workloads, continuous integration and deployment.